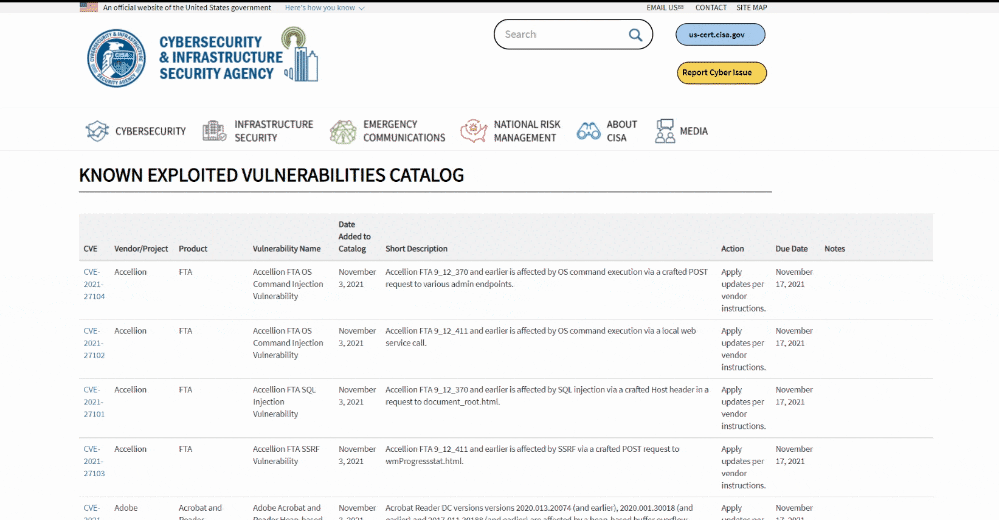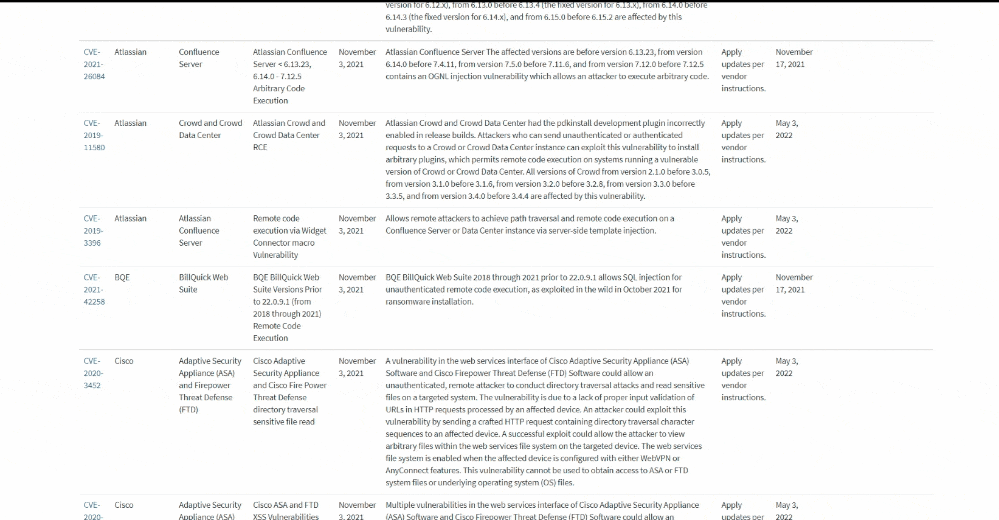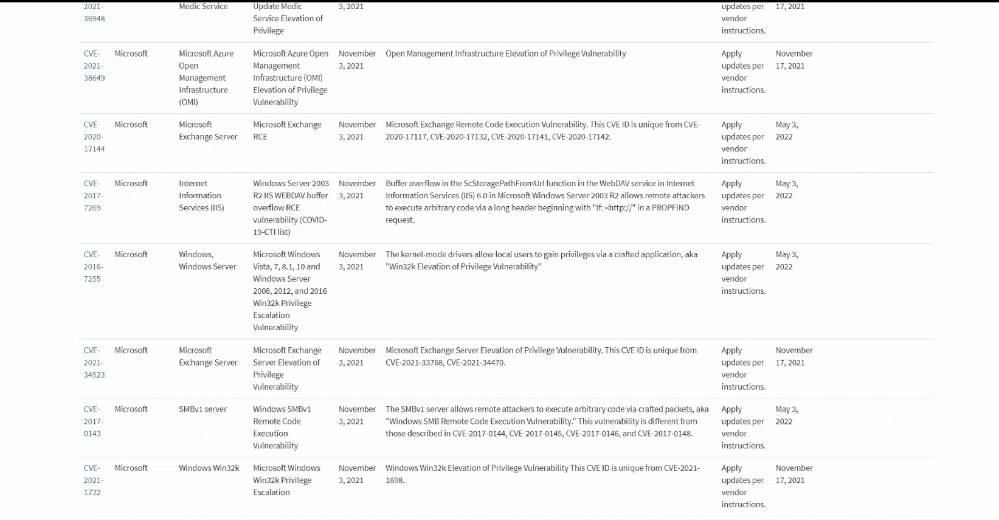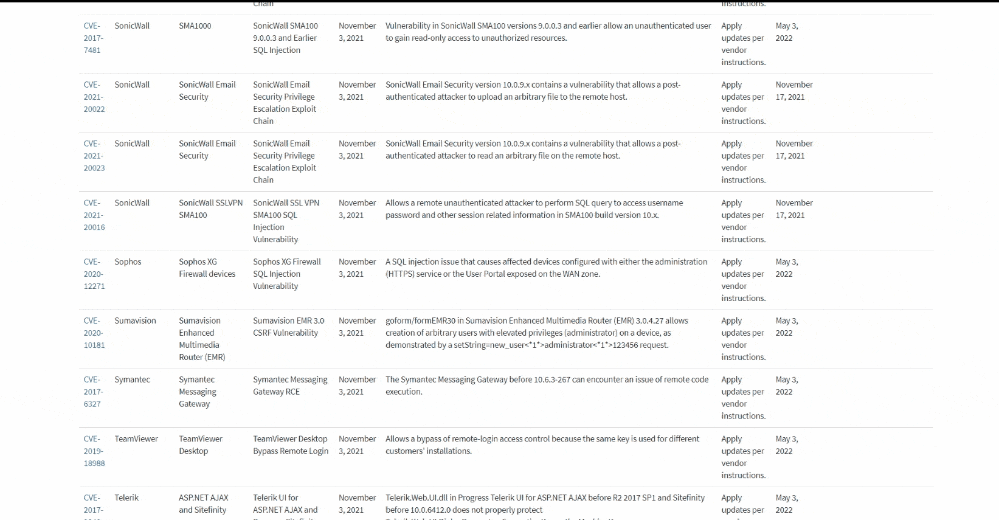
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has published a catalog of vulnerabilities, including from Apple, Cisco, Microsoft, and Google, that have known exploits and are being actively exploited by malicious cyber actors, in addition to requiring federal agencies to prioritize applying patches for those security flaws within “aggressive” timeframes.
“These vulnerabilities pose significant risk to agencies and the federal enterprise,” the agency said in a binding operational directive (BOD) issued Wednesday. “It is essential to aggressively remediate known exploited vulnerabilities to protect federal information systems and reduce cyber incidents.”
About 176 vulnerabilities identified between 2017 and 2020, and 100 flaws from 2021 have made their way to the initial list, which is expected to be updated with additional actively exploited vulnerabilities as and when they become known provided they have been assigned Common Vulnerabilities and Exposures (CVE) identifiers and have clear remediation action.
The binding directive mandates that security vulnerabilities discovered in 2021 — those tracked as CVE-2021-XXXXX — be addressed by November 17, 2021, while setting a patching deadline of May 3, 2022 for the remaining older vulnerabilities. Although the BOD is primarily aimed at federal civilian agencies, CISA is recommending private businesses and state entities to review the catalog and remediate the vulnerabilities to strengthen their security and resilience posture.
The new strategy also sees the agency moving away from severity-based vulnerability remediation to those that pose significant risk and are being abused in real-world intrusions in light of the fact that adversaries do not always necessarily bank only on ‘critical’ weaknesses to achieve their goals, with some of the most widespread and devastating attacks chaining multiple vulnerabilities rated ‘high,’ ‘medium,’ or even ‘low.’
“This directive does two things. First, it establishes an agreed upon list of vulnerabilities that are being actively exploited,” Tim Erlin, Tripwire’s VP of Strategy, said. “Second, it provides due dates for remediating those vulnerabilities. By providing a common list of vulnerabilities to target for remediation, CISA is effectively leveling the playing field for agencies in terms of prioritization. It’s no longer up to each individual agency to decide which vulnerabilities are the highest priority to patch.”
Source: thehackernews.com/